Protection of confidential information
in your company
Secure documents, control access, and be certain that your data won’t end up in the wrong hands — even outside the company.
All without disrupting users' daily work.
Do you know where your systems have gaps?
Information protection starts with control
Backups are not enough. Data travels outside your company — via email, drives, and the cloud.
Information protection is control over who opens files, who has access, and what they can do with them.
Thanks to classification and encryption, you can be sure that the data won’t end up in the wrong hands — even outside the organization.

Control starts with visibility
You can't protect what you can't see. With centralized access rights management, you know exactly who has access to each file — and you can change or revoke it at any time.


Access doesn’t mean full freedom
Information protection goes beyond simply blocking or allowing actions. You decide whether a user can open, edit, forward, or print a file — even after they’ve left the company. You set the limits.


Protection that works beyond your server
Documents secured with SealPath follow your rules — no matter where they go. You can revoke access anytime, track openings, and be sure the data won’t fall into the wrong hands.


Security that works in the background
The system integrates with everyday work environments — no training or tool changes required. Users work as usual, while document protection runs automatically in the background, without interruptions.


PROVEN TOOLS FOR INFORMATION PROTECTION
Protect confidential data and regain control
Implementing DLP solutions means real control over where your data is, who has access to it, and what they can do with it. Thanks to classification, encryption, and access control, you eliminate the risk of leaks and build a secure environment — even beyond your company.


Secure
documents
Confidential files are protected automatically — thanks to encryption and access control, even outside your organization.

Full control
over flow
You know exactly who has access to what and what they can do with it — even beyond the company.

Protection without changing habits
The system works in the background — users work as usual, with security handled automatically.

Protection without changing habits
The system works in the background — users work as usual, with security handled automatically.
SealPath
Information protection that works always and everywhere
Grant access, set time limits, block copying, printing or forwarding. And if needed — revoke permissions with a single click.
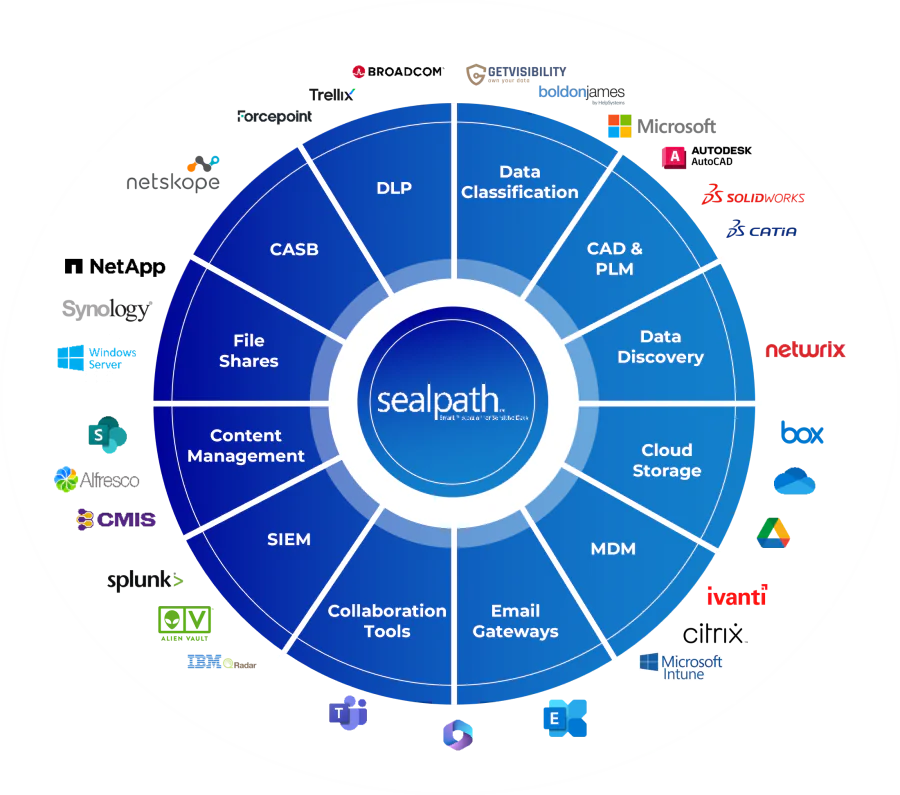
What is SealPath?
SealPath is an intelligent document protection solution that lets you control access to information — regardless of where the file is stored or who opens it.
Instead of securing only computers or company networks, SealPath protects the content itself. Documents “carry” security rules with them, even outside the organization — via email, cloud, or private devices.
You decide who has access to the file, for how long, and what they can do with it — without involving your IT team. Everything works automatically, in the background, without changing how your team works.


What is SealPath?
SealPath is an intelligent document protection solution that lets you control access to information — regardless of where the file is stored or who opens it.
Instead of securing only computers or company networks, SealPath protects the content itself. Documents “carry” security rules with them, even outside the organization — via email, cloud, or private devices.
You decide who has access to the file, for how long, and what they can do with it — without involving your IT team. Everything works automatically, in the background, without changing how your team works

How does SealPath help in daily work?
SealPath works where traditional protections end — in everyday document circulation: between employees, clients, emails, and the cloud. It protects what truly matters — offers, client data, contracts — without extra effort or changing your team’s workflow.
You no longer have to wonder who has access to a file and what they can do with it. You gain control, peace of mind, and time — because security just works in the background.
See how SealPath simplifies daily work and where it really makes a difference:
You decide who has access, for how long, and what they can do with the file. If needed, you can revoke access with a single click.
Even if a document leaves the company, no unauthorized person will open or forward it. You set the rules — always.
No need to train employees on new systems. SealPath works in the background, automatically securing everything according to policy.
The system logs who accessed the documents, when, and how — so you have ready-to-use reports for compliance inquiries.
You get full visibility: who opened the file, when, how many times, and from which device. You can respond in real time.
SealPath integrates with Microsoft 365, AD, and Windows environments. No new infrastructure or IT department required.

How does SealPath help in daily work?
SealPath works where traditional protections end — in everyday document circulation: between employees, clients, emails, and the cloud. It protects what truly matters — offers, client data, contracts — without extra effort or changing your team’s workflow.
You no longer have to wonder who has access to a file and what they can do with it. You gain control, peace of mind, and time — because security just works in the background.
See how SealPath simplifies daily work and where it really makes a difference:
You decide who has access, for how long, and what they can do with the file. If needed, you can revoke access with a single click.
Even if a document leaves the company, no unauthorized person will open or forward it. You set the rules — always.
No need to train employees on new systems. SealPath works in the background, automatically securing everything according to policy.
The system logs who accessed the documents, when, and how — so you have ready-to-use reports for compliance inquiries.
You get full visibility: who opened the file, when, how many times, and from which device. You can respond in real time.
SealPath integrates with Microsoft 365, AD, and Windows environments. No new infrastructure or IT department required.
See how SealPath works
SealPath allows you to manage access to confidential documents in a simple, effective, and fully controlled way — from start to finish. Instead of watching people, you enforce rules. Here’s how the process looks step by step:

You create a documentwith sensitive data
You work as usual — in Word, Excel, AutoCAD or PDF. The system works in the background.

You mark the document as sensitive
The system automatically assigns protection or allows you to do it manually.

You set access and usage rules
You decide who can open the file, what they can do with it, and how long the access should last.

You share the file securely
The document is sent by email, cloud or pendrive — under the defined security policy.

You monitor access and activity
You have a log of who accessed the file, when, and how. You’ll see any violations.

You change or revoke access at any time
One click and the document becomes inaccessible — even if it already left the company.
Are you sure your data is secure?
Order an
IT Security Audit
Don’t wait for something to go wrong. One mistake, an accidental click, or an unnoticed vulnerability can cost you: data, customers, reputation. An IT audit will help identify threats before they turn into a cyber incident.

Frequently Asked Questions about
Information Protection in a Company
Before you decide to implement SealPath or monitoring, it’s worth knowing a few key facts.
Here are the most common questions asked by business owners:
