Data protection technologies
from trusted vendors
We select only solutions that truly enhance IT security.
Discover the hardware and technologies trusted by industry leaders.


Veriato
THREAT DETECTION
An expert in monitoring user activity (UEBA) and detecting insider threats. Veriato solutions provide insights into employee behavior, anomaly analysis, and rapid response to potential incidents. These tools are valued by organizations that prioritize data security and regulatory compliance.


What does Veriato offer?
A comprehensive solution for advanced monitoring of internal user activity (UEBA). It enables real-time behavior analysis, identification of suspicious patterns, and alerts in case of insider threats. Veriato Cerebral supports organizations in building internal detection and response mechanisms—before a security breach occurs.
A lightweight, fast-to-deploy tool for day-to-day computer monitoring. Ideal for assessing team performance, employee productivity, and operational activity. Veriato Vision is a perfect choice for organizations seeking visibility without overloading systems or IT resources. Activity can be monitored via a simple, web-based interface.
A fully covert solution—operating like a "black box" for organizational security. It records user activity without revealing its presence—until an anomaly or incident is detected. Enables retroactive investigation of suspicious events and provides solid evidence in case of disciplinary or legal action.
A central platform for managing digital security at scale. It offers comprehensive control over multiple endpoints across locations, with full reporting, analytics, and administration from a single dashboard. Veriato 360 is the ideal tool for larger organizations that need a centralized and scalable solution for managing insider risk.
A specialized forensic tool for immediate workstation analysis—without the need for permanent software installation. Designed for rapid response in crisis scenarios, policy violations, or incident audits. It delivers detailed insights into user activity history without impacting system performance.
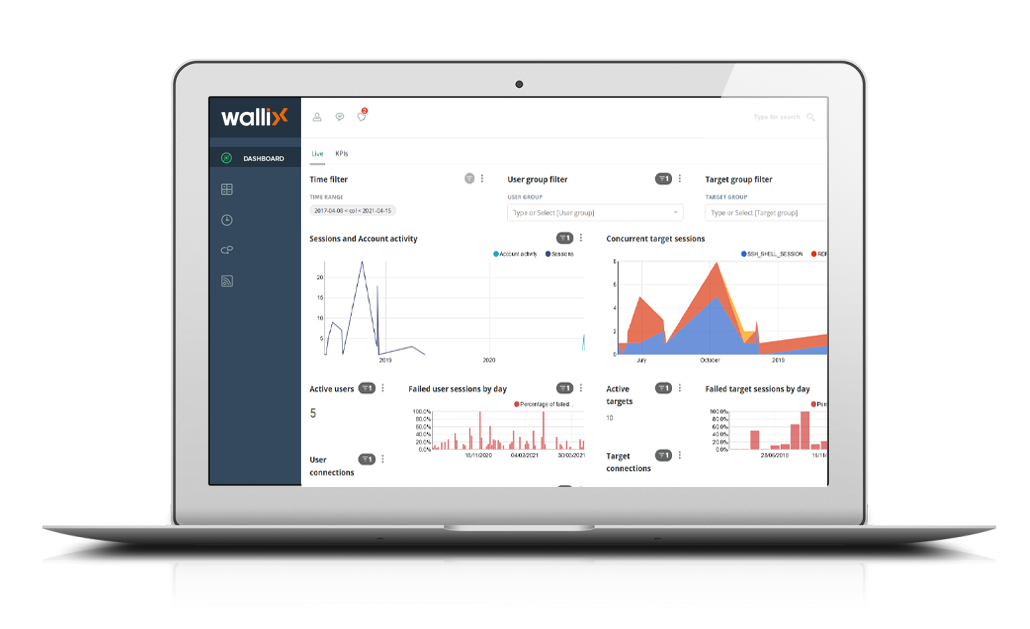

Wallix Bastion
ACCESS CONTROL
Wallix is a European leader in privileged access management (PAM), focusing on protecting administrator accounts, servers, databases, and critical systems.Their flagship solution – Wallix Bastion – provides full visibility and control over who accesses what, when, and why within the IT environment.
The system supports session recording, real-time access auditing, and automated enforcement of security policies.


Key features at a glance
Privileged Password Management
Automated management of the full password lifecycle: complexity, rotation, and security. Eliminates the risk of theft, sharing, or unauthorized access—without the need for manual intervention.
Secure Access to Web Applications
Records video sessions in color along with transcripts and metadata. Every session is logged, replayable, and analyzed for compliance and user activity traceability. This ensures full visibility into privileged actions without deploying any additional agents.
Web Session Monitoring & Access
Web Session Manager enables secure access to web apps without modifying the app itself. Everything runs through the browser—no need to install additional software or change configuration.
Secure Machine-to-Machine Communication
Application-to-Application Password Management (AAPM) removes hardcoded credentials from scripts and config files. Automates credential handling and prevents leakage – no manual input required.
Real-Time Access Control
Grants access to authorized users based on permissions policy. All connections are monitored and recorded in real-time—giving full visibility to system administrators.
Agentless Integration
Seamless integration with no agent installation required. Works without changes to industrial or business applications and is ready for deployment in any OS environment.


Macrium Reflect
BACKUP SOLUTIONS
Macrium is a recognized provider of advanced backup and fast data recovery software. Its solutions are trusted by IT departments in large enterprises as well as by individual users. Macrium Reflect offers comprehensive protection for systems, disks, and files—with precise task scheduling, encryption, and full support for both physical and virtual environments.


Key features of Macrium Reflect
Macrium Reflect Home
- Full disk and partition backup (system imaging)
- Automated backup scheduling
- System recovery functionality
- AES encryption and ransomware protection
- Support for differential and incremental backups
- Creation of rescue media (USB/DVD)
Macrium Reflect Workstation
- Advanced Windows system backup for businesses
- Protection against data loss on endpoints
- Encryption, scheduling, and email notification support
- Support for differential, incremental, and full backups
- VSS (Volume Shadow Copy) integration
- Integration with Macrium Site Manager
Macrium Reflect Server
- Backup of physical and virtual servers
- Support for Hyper-V and RAID environments
- Automated backup and recovery process
- Comprehensive server data protection with minimal downtime
- Flexible storage options: local, NAS, or network
- System restore to dissimilar hardware (ReDeploy)
Macrium Site Manager
- Centralized management of all backup tasks
- Intuitive interface for task scheduling and monitoring
- Multi-device management from a single console
- Backup status reporting and alerting
- Integration with Workstation and Server products
- Scalable for both SMB and enterprise environments
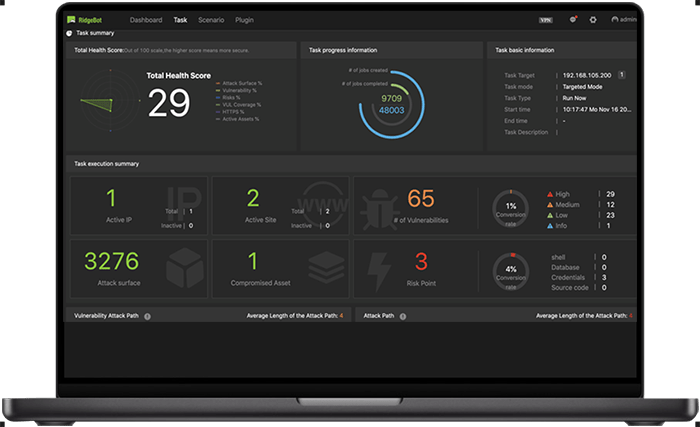
Ridge Security
SECURITY TESTING
Ridge Security is a company specializing in the automation of penetration testing. Its flagship product, RidgeBot, combines advanced attack simulation with risk analysis, enabling organizations to quickly, repeatedly, and at scale test the resilience of their IT systems. RidgeBot solutions are used by security and compliance teams to identify, verify, and prioritize vulnerabilities—without the need for manual intervention by experts.

Key Software Capabilities

Automated Penetration Testing
RidgeBot autonomously conducts the full attack cycle—from reconnaissance to exploitation of discovered vulnerabilities.

Real Threat
Simulation
Applies real-world cyberattack techniques to assess the actual resilience of IT systems.

Vulnerability
Identification
Detects vulnerabilities, evaluates risk levels, and suggests prioritized remediation actions.

Safe Testing
Environment
All testing is performed in a controlled manner, eliminating the risk of disrupting production systems.

Compliance and
Audit Support
Helps meet regulatory requirements such as GDPR, ISO 27001, and NIS2 through regular reports and logs.
SIEM and Ticketing
Integration
Easily integrates with leading monitoring and incident management platforms for seamless response workflows.
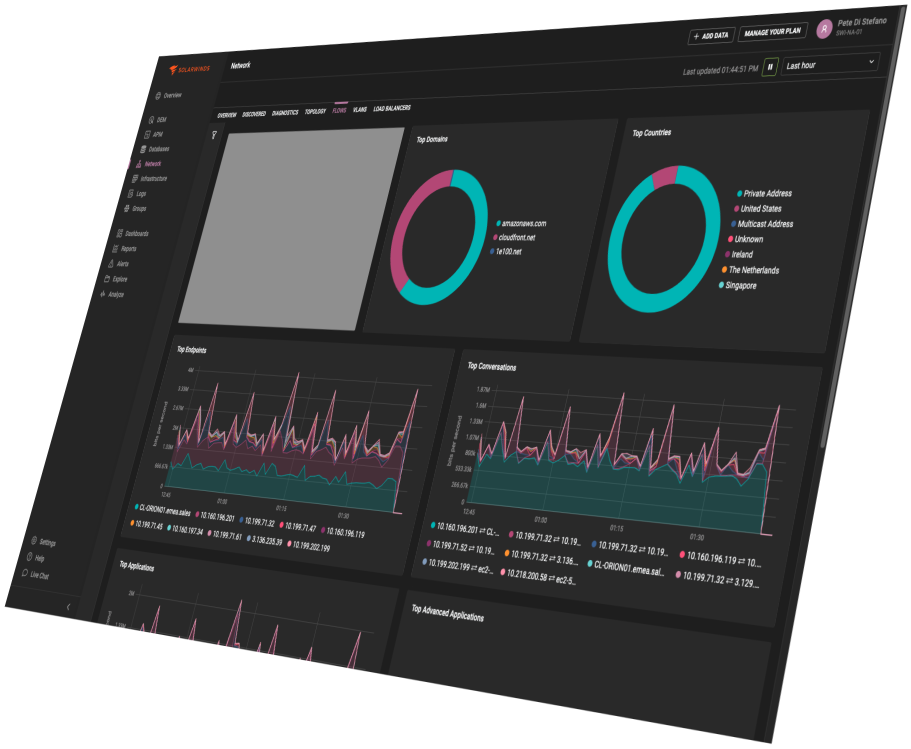

SolarWinds
User MONITORING
SolarWinds is a globally recognized provider of specialized software for monitoring, managing, and optimizing IT infrastructure—both on-premises and in the cloud. Their tools are trusted by IT teams across organizations of all sizes, from small businesses to large financial and public sector institutions.


Discover What SolarWinds Can Do
With SolarWinds, you can monitor the status of servers, network devices, applications, and databases in real time. The system detects failures, overloads, and unusual behavior before they can impact business continuity.
SolarWinds collects logs from various sources (servers, applications, network devices) and correlates them, enabling quick identification of incidents, errors, and threats. Advanced filters and alerts help automate response.
Allows you to monitor CPU, memory, bandwidth usage, and application load in real time. This gives you a full view of infrastructure health and lets you plan resource expansion based on real data.
SolarWinds supports compliance with GDPR, ISO 27001, and NIS2 standards. It provides ready-made reports that help demonstrate control over access, incidents, and security policies—especially important in regulated environments.
The software supports integration with SIEM, ticketing systems, cloud platforms, and DevOps services. It automates repetitive administrative tasks, speeding up IT team workflows and reducing the risk of human error.

SecPoint
Security Testing
SecPoint is a European manufacturer that says “no” to complex deployments and “yes” to effective network protection. Its devices and software offer ready-to-use solutions that combine firewall, vulnerability scanning, IDS/IPS, Wi-Fi protection, and log analysis—all in one. This gives you not only full control, but also an edge against cyber threats—without the need to hire a dedicated team of specialists.
SecPoint is the perfect choice for companies that want to comprehensively protect their IT infrastructure but lack the time or budget for complex enterprise-class systems. Its simple interface, rapid deployment, and real effectiveness make it a preferred solution for both private companies and public sector institutions.

One device – multiple layers of protection
Instead of combining several different tools, invest in a single one that does it all. SecPoint is a multifunctional platform for network protection, vulnerability scanning, and threat monitoring – ready to work right after deployment. Ideal for companies looking to enhance security without hiring additional specialists or investing in complex infrastructure.
Firewall, IDS, and
SIEM in one
Instead of three tools – just one. SecPoint combines advanced firewalling, intrusion detection, and log analysis in a single platform.
Vulnerability scanning with zero configuration
Automatically detects vulnerabilities in systems, servers, and applications – no need to manually define rules.
Enterprise-class
Wi-Fi protection
Secure management of wireless networks – detects rogue APs, Evil Twin attacks, and unauthorized connections.
Audit readiness
in a few clicks
Generates clear reports compliant with GDPR, ISO 27001, and PCI-DSS – ideal for both internal and external audits.
Fast deployment without
a SOC team
SecPoint is operational right after installation. The intuitive interface allows security management even without specialized personnel.
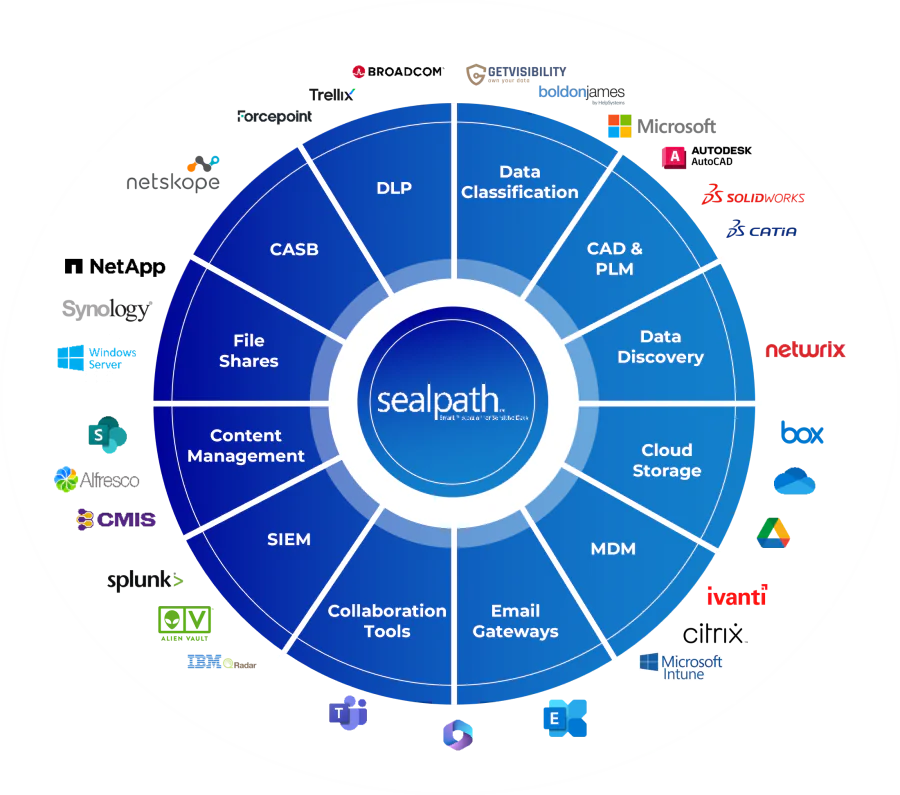
SealPath
INFORMATION PROTECTION
SealPath is an advanced solution in the field of DRM (Data Rights Management) that enables full control over documents – even after they leave your organization. Thanks to file-level encryption and dynamic access policies, SealPath protects data from unauthorized access, copying or sharing – whether in the office, in the cloud or outside the corporate network. Ideal for organizations that need to combine collaboration with information security.

What sets SealPath apart from other solutions
Automatic classification and encryption
SealPath automatically assigns sensitivity levels to documents and protects them in accordance with the security policy – without user intervention.
Full control over information flow
You can change at any time what can be done with a document – read, edit, forward, print or revoke access. Dynamic permissions ensure data stays protected.
Data protection outside the organization
Documents remain protected even after leaving the corporate network – external users must authenticate, and access can be time-limited.
Security without changing habits
SealPath works in the background, integrating with Windows and Microsoft 365 – end users don’t have to change their daily habits.
Audit and document usage tracking
Administrators can see who, when and how a document was accessed – ensuring GDPR compliance and facilitating audits.
Constant access despite staff turnover
Access can be revoked or transferred at any time – thanks to persistent encryption, information retains ownership even after an employee leaves.


RiskRecon
SECURITY TESTING
RiskRecon is a platform for identifying risks (vulnerabilities, configuration errors, exposure of sensitive data, etc.) within an organization and its partners. It automatically presents a risk matrix and maps it to accepted standards (e.g., DORA/NIST/CIS), enabling the effective implementation of automated remediation plans for the entire organization and supply chain.
Each repair process is continuously monitored by artificial intelligence in terms of timing and effectiveness.


How RiskRecon Secures the Entire
Risk Management Process


Unitrends
Backup Solutions
Unitrends, with over 30 years of experience in data protection, is a global provider specializing in backup, disaster recovery, and business continuity solutions. It offers modern platforms available as physical appliances, virtual machines, software, and cloud services – all designed with maximum simplicity, efficiency, and security in mind.
Thanks to full integration with leading environments (VMware, Hyper-V, NAS, Microsoft, Linux/Unix), Unitrends eliminates the complexity of backup management and allows companies to focus on what matters most – stable business growth. Unitrends solutions stand out with rapid recovery, advanced ransomware protection, automated recovery testing, and exceptional cost efficiency (TCO).


why Unitrends?
Enterprise-grade data protection in every form.
Unitrends solutions provide comprehensive data protection: from local backups to cloud backups, recovery testing, and ransomware protection. Discover the key benefits that set Unitrends apart from the competition.
Unitrends enables near-instant recovery of physical and virtual environments. Thanks to intelligent snapshots and integration with hypervisors, restoring a server or virtual machine takes only a few minutes — with no manual configuration required. This is crucial for maintaining operational continuity in any organization.
The system detects signs of ransomware attacks and immediately creates secure backups before the data is encrypted. Additionally, backups are stored in an immutable form, preventing tampering even in the event of an advanced attack.
Unitrends supports simultaneous local backups, Unitrends Cloud, and public clouds (Amazon S3, Google Cloud, Azure). This allows you to flexibly decide where and how to store data — with your SLA, RTO, and budget in mind.
The Disaster Recovery Verification feature automatically tests backups to confirm that the data can actually be restored.Tests run cyclically, in the background, without involving the IT team. This gives you real confidence that your backups are fully functional.
Unitrends allows fast and reliable NAS system backups (NetApp, EMC, QNAP, and others) without the need for the NDMP protocol. Importantly, file attributes and permissions (ACLs) are preserved, significantly simplifying the recovery process.
Unitrends solutions come as ready-to-use appliances with a preinstalled system, deduplication, WAN acceleration, and cloud integration. Everything works right out of the box. No hidden licensing fees and full automation mean a much lower TCO compared to competitors.


Fox-IT
data diodes
(Fox Crypto) is a pioneer in high-assurance security solutions for the highest sensitivity levels of industrial systems (OT) and closed networks.
The dedicated data diode Fox DataDiode Ruggedised/EAL7+ guarantees one-way data flow, eliminating the risk of unauthorized communication — while still allowing for secure transfer of logs, reports, and updates.
The device is certified with Common Criteria EAL7+, NATO SECRET, and COSMIC TOP SECRET, making it one of the few solutions with such extremely high reliability.


See what Fox-IT can do for you
Fox‑IT’s solution leverages hardware‑enforced unidirectional communication, meaning data can only flow one way — for example, from an OT (operational technology) network to IT systems. This completely eliminates the risk of reverse attacks, tunneling, or malware takeover. Ideal for SCADA/ICS systems, classified networks, and other high‑security environments.
The Fox Data Diode enables secure export of logs, alerts, and telemetry data from operating systems, industrial devices, and security‑monitoring platforms. This supports centralized reporting without exposing OT networks to attack. Typical use cases include log forwarding to SIEMs, data export to SOCs, and compliance oversight.
Using specialized transfer modes, it safely delivers updates — such as anti‑virus databases, IDS signatures, or system patches — to isolated OT environments. All this occurs without creating a return channel, preserving security while maintaining operational compliance.
Fox‑IT’s Data Diode is certified Common Criteria EAL7+ — the highest security rating for IT systems. Additionally, the device meets NATO SECRET, EU SECRET, and TEMPEST (EM emission reduction) standards. This makes it highly suitable for military, government, energy, and industrial sectors.
Fox‑IT supports a wide range of protocols used in both IT and OT networks: Syslog, FTP, SMB, Modbus, OPC, SNMP, NTP, SFTP, XML/REST. This ensures easy integration with most devices and systems — without needing structural changes. The solution can function as a transparent relay or convert communication formats as needed.










