User Monitoring and Threat Analysis
Gain full insight into user activity, detect internal threats, unauthorized access, and mistakes — before they become incidents. User and Entity Behavior Analytics (UEBA) helps protect the company from the inside.
Did you know what’s really happening in your company?
User monitoring and threat analysis reveal risks before they turn into incidents
Instead of reacting after a problem occurs — react before it affects your company. Monitoring user activity and behavior (UEBA) allows early detection of anomalies and threats such as sabotage, negligence, data leaks, or malicious actions. With behavior analysis, you see what’s going on and act based on facts.

The system sees it before it happens
Thanks to User Behavior Analytics (UBA), you'll notice deviations from the norm — suspicious searches, data copying, or access outside working hours. One warning signal is enough to act before it escalates into an incident.

Not every attack is visible immediately
but the system will catch it
Veriato monitors user activity and analyzes behavioral patterns. When someone starts acting suspiciously — like exporting data or bypassing security — you receive an early warning signal. Before things get serious.

React before it’s too late
The system detects risky actions in real time — such as unauthorized access or suspicious data copying. Instant alerts allow you to block access immediately, before the information leaves your organization.


Internal data leaks mean real losses
When an employee causes a data breach, the cost can reach hundreds of thousands of złoty — not to mention lost customer trust. User monitoring and behavior analysis let you detect threats early, before the damage is done.


Effective User Monitoring
Gain insight into employee actions and protect the company from within
Advanced user behavior and threat analytics (UEBA) help detect anomalies, assess risks, and act based on facts — not assumptions.

Continuous
monitoring
See what’s happening in the systems — in real time.

Early detection of anomalies
Detect when something is wrong — even before it’s too late.

Data for
decisions
Make decisions based on facts and data, not intuition or suspicions.

Data for
decisions
Make decisions based on facts and data, not intuition or suspicions.
Veriato
User monitoring that reveals threats before they become a problem
If you want to know what's happening in your company, or you're required to do so — meet Veriato.
This tool helps monitor employee behavior, detect threats, ensure security and compliance — from HIPAA to ISO.
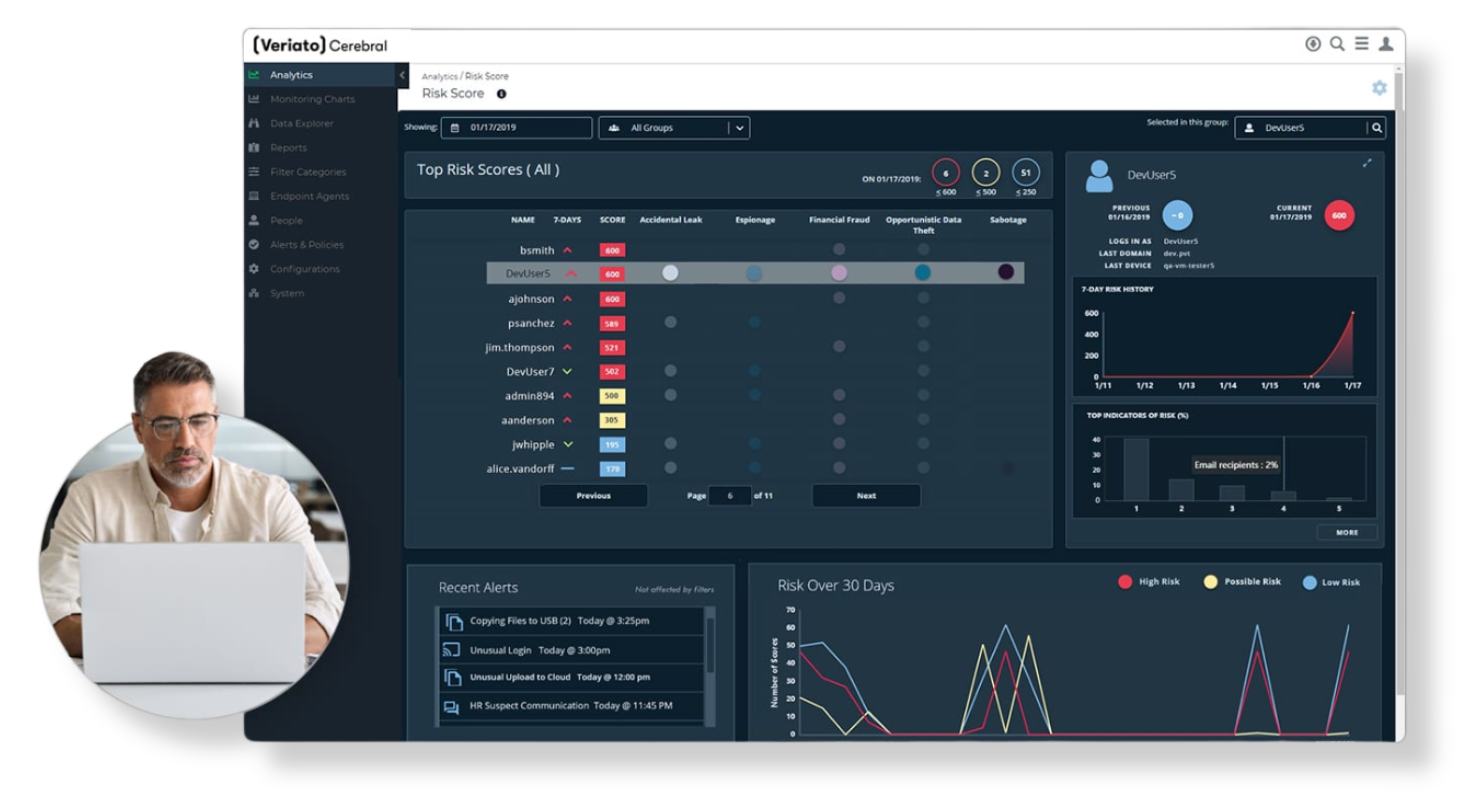
What is Veriato?
Veriato is advanced monitoring software for organizations that helps detect insider threats, analyze employee behavior, and build a culture of security.
It operates discreetly, tracking user activity on both PC and Mac computers, detecting anomalies, and supporting compliance with regulations such as GDPR and HIPAA.
Veriato is used wherever data security and employee accountability are critical — from small businesses to hospitals and public institutions.


How does it help in daily work?
Veriato is not just a control tool — but an awareness tool. It helps detect threats and eliminate misunderstandings. It gives managers a better understanding of how work is done.
You don’t need to watch everything — the system learns and alerts you only when something abnormal happens.
It fits into processes and integrates with existing systems.
You don’t have to guess. Veriato shows exactly how employees spend their time — how much goes toward specific tasks versus aimless browsing or clicking.
If someone suddenly starts behaving differently — for example, their performance drops, they avoid tasks, or begin using suspicious software — you have the chance to respond before it turns into a crisis.
Thanks to detailed reports, you know who deserves recognition, where a conversation is needed, and where something more serious might be hiding. You have a solid foundation for action — not just intuition.

How does it help in daily work?
Veriato is not just a control tool — but an awareness tool. It helps detect threats and eliminate misunderstandings. It gives managers a better understanding of how work is done.
You don’t need to watch everything — the system learns and alerts you only when something abnormal happens.
It fits into processes and integrates with existing systems.
You don’t have to guess. Veriato shows exactly how employees spend their time — how much goes toward specific tasks versus aimless browsing or clicking.
If someone suddenly starts behaving differently — for example, their performance drops, they avoid tasks, or begin using suspicious software — you have the chance to respond before it turns into a crisis.
Thanks to detailed reports, you know who deserves recognition, where a conversation is needed, and where something more serious might be hiding. You have a solid foundation for action — not just intuition.
Choose what you really need
Tailor Veriato to your organization — whether you need full behavior analytics, protection against data leaks, or to document access.
Veriato Cerebral
Advanced monitoring, behavioral analysis, and insider threat alerts — before it gets serious.
Veriato Vision
Visibility into daily work. A lightweight computer monitoring tool — perfect for evaluating productivity and organization.
Veriato Recon
The black box of cybersecurity. It works discreetly in the background, registers activity, and waits for your signal to reveal only what’s necessary.
Veriato 360
Comprehensive employee monitoring. Ideal for larger teams — gives insight into actions, controls the use of company resources, and allows centralized management.
Veriato Investigator
When you need to look deeper. A lightweight forensic tool — for investigating specific incidents, without installing the full platform. Zapytaj ChatGPT
Are you sure your data is safe?
Request an IT Security Audit
Don't wait until something happens. One mistake, accidental click, or unnoticed gap can cost you your data, your clients, and your reputation. An IT audit can reveal threats before cybercriminals do.

SOLARWINDS
Detect threats, respond automatically – before they escalate into an incident
Want to know what’s happening in your infrastructure – before it becomes dangerous?
SolarWinds is an advanced SIEM-class tool that analyzes logs in real time, detects anomalies, and instantly triggers responses to threats.
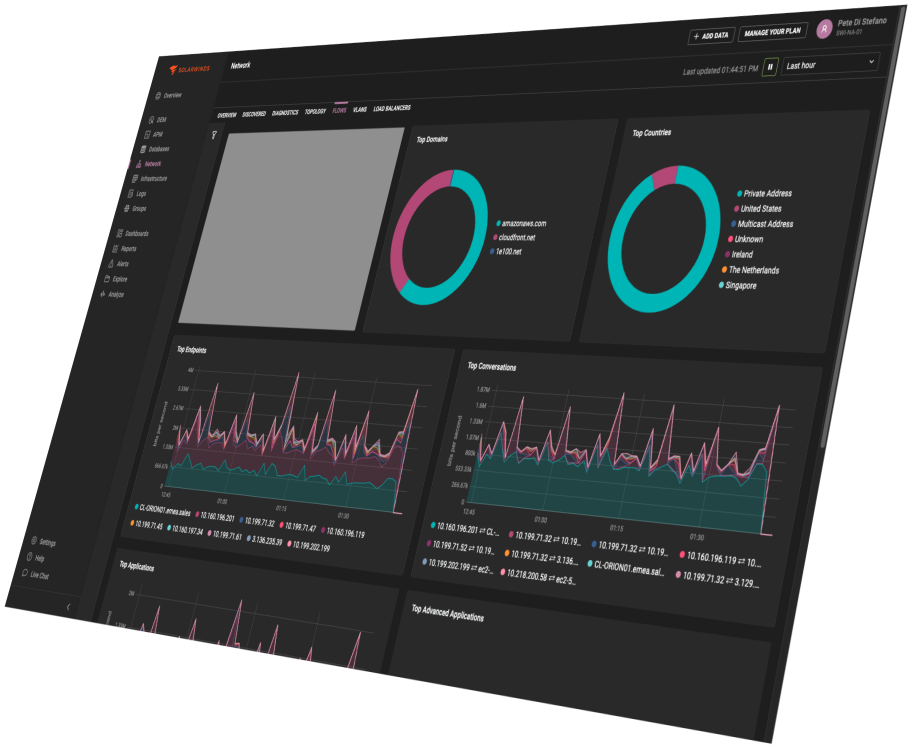
What is SolarWinds?
SolarWinds is an intelligent SIEM platform designed with full visibility and control over IT environment events in mind – both on-premises and in the cloud. The system analyzes large volumes of data in real time – from system logs and network events to user activity.
This enables it to quickly detect anomalies, pinpoint threat sources, and trigger predefined responses – before the incident impacts your organization.
SolarWinds scales well – from mid-sized firms to large enterprise environments.
It not only protects your infrastructure but also helps you meet compliance requirements such as NIS2, ISO 27001, and GDPR, without the need to significantly expand your security team.


How does SolarWinds support your team on a daily basis?
SolarWinds simplifies incident analysis, shortens response time, and provides context – all in one view. Instead of clicking through logs and alerts, the IT team sees related events and clear visualizations.
It acts like a digital SOC analyst assistant – identifying the source of the problem, suggesting responses, and even triggering automated remediation scenarios. Below are a few specific use cases:
Instead of drowning in hundreds of alerts from different systems, SolarWinds automatically groups and correlates events from logs, networks, systems, and applications.You get a consistent, organized view of the situation that helps you understand exactly what happened – and why.
By analyzing both historical and real-time data, SolarWinds identifies alarming trends before an incident occurs. For example: an increased number of failed logins, unusual network activity, or a sudden spike in server load – these are signals SolarWinds detects instantly.
SolarWinds not only alerts you to threats but can also automatically trigger remediation procedures. This allows you to eliminate risks before they affect users or customers. Your team gains valuable time and can focus on strategy instead of firefighting.
Key capabilities at a glance
Network and device monitoring
Monitor bandwidth, availability and failures – in real time, with automated alerts.
Server and application management
Track system and service health – detect drops in performance before users notice them.
Advanced log analysis
Event correlation, threat visualization, and automated security analysis.
Database monitoring
Identify slow SQL queries, overloads, and database errors – improve data processing performance.
Virtual infrastructure management
Monitor physical, virtual, and cloud environments – switch easily between tools.
Automated response and reporting
Create remediation scenarios, reports, and alerts – meet ISO 27001, NIS2 and GDPR requirements.
Frequently Asked Questions
about User Monitoring
Still have doubts about implementing Veriato or any user monitoring solution?
We answer the most common questions — without avoiding difficult topics.
